IP CCTV
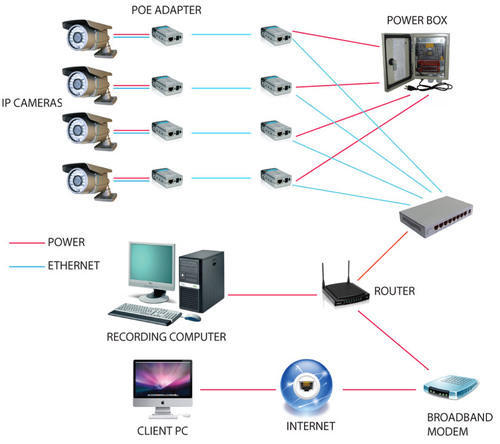
at SMI we believe IP cameras are the future of security camera technology. We rigorously test and review each IP camera model we sell to ensure it performs to specifications, and is easy to integrate with our network video recorders.
Most network cameras we sell have PoE connectivity built-in, making them easy to use with any NVR with built-in PoE switch. . Although there are several advantages to using IP security cameras, the main ones are 1) resolution support beyond 2K, and 2) easy connectivity with CAT5e or better network cabling.
For customers looking to build a future proof security cameras system, IP cameras are the best choice. Be sure to browse through our selection of IP camera systems, especially our 4K security camera systems which feature the best resolution cameras money can buy combined with our professiona