Security Concern!
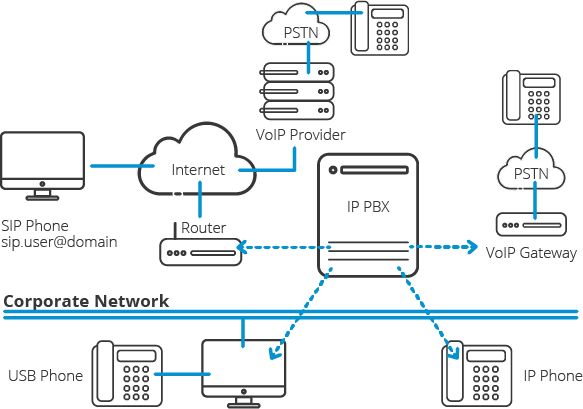
When malicious attacks occurred on siloed networks, attackers could only access whatever data was on the particular network they broke into; telecommunications, closed-circuit TV and PCs ran on different networks, so attackers could access only one resource at a time. Once all those resources used the same infrastructure, an attacker could access all of them through a single access point.
Originally, the top concern was eavesdropping, or the unauthorized interception of VoIP, messaging other traffic. UC endpoints, whether desktops, laptops, or IP phones, all connect to the data network, and can be tapped by compromising the network anywhere along the data route.
IP telecommunications providers around the world lose hundreds of millions of dollars annually due to stolen services through toll fraud. Converged voice and video traffic typically uses the Session Initiation Protocol (SIP) to control calls, but the actual media stream for a call is separate from that control stream. It is possible, therefore, to use SIP to spoof the call manager about what kind of call it is controlling. For example, the perpetrator might tell the call manager that a call will be voice-only, but then stream high-definition video instead, essentially defrauding the system owner of the higher revenues for the video traffic.